Introduction
Payment Manager comes with an identity provider component built into the product, which serves as a repository of identities and allows for the granting of role-based access to users of the Payment Manager portals (the Connection Wizard, the Transfers Overview, and the Technical Dashboard). User access management within the context of Payment Manager means:
-
creating user accounts from scratch or tying into an existing Active Directory/LDAP user database by federation
-
assigning roles to users or mapping roles from an existing user database to roles created in Payment Manager
-
group membership definition
-
setting up an authentication method for users
-
policy management for passwords and one-time passcodes
-
account recovery and user credentials management
Payment Manager leverages the Keycloak identity provider and implements the OpenID Connect authentication protocol. OpenID Connect is an identity layer on top of the OAuth 2.0 protocol, which enables applications to authenticate end users and obtain information about them.
The following diagram illustrates where the identity provider is situated within Payment Manager architecture.
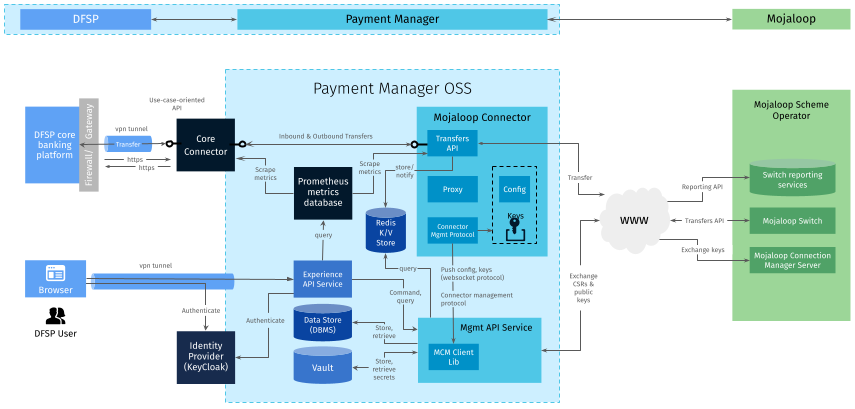
When there is an existing OAuth 2.0 or OpenID Connect compliant identity service that the Digital Financial Services Provider (DFSP) already has, then that may be used in place of Keycloak. Otherwise, the identity provider is Keycloak.
In the case of an on-premise deployment, there will be one Keycloak per Payment Manager instance. For a cloud-hosted SaaS deployment, the Keycloak instance may be shared across multiple Payment Manager instances.