Getting started with Keycloak
Admin Console
The Admin Console is the Keycloak user interface that enables administrators to manage user accounts and access to Payment Manager.
As an administrator of Payment Manager user accounts, you need the following:
-
An admin account to the Admin Console.
This is created by the Infrastructure team deploying Payment Manager. The admin account must be set up so that it has permissions to manage only the relevant realm. -
The URL to the Admin Console.
This is also provided by the Infrastructure team. -
VPN access to the Admin Console.
For further information on the Admin Console, see section Admin Console in the Keycloak Server Administration Guide.
Prerequisites
To be able to add user accounts to manage access to Payment Manager, the Payment Manager application itself must be set up in Keycloak first:
-
A realm or realms must be configured.
-
The Payment Manager user interface must be registered as a client of Keycloak.
This section provides details about these two prerequisites.
Realms
In the case of an on-premise deployment, Payment Manager comes with an out-of-the-box Pm4ml realm (Pm4ml stands for Payment Manager for Mojaloop). A realm can be thought of as an isolated domain, in this case, that domain is the Payment Manager application. Anything within the Pm4ml realm relates to the Payment Manager instance.
In the case of a SaaS cloud deployment, there will always be one realm per DFSP.
The Pm4ml realm has some pre-configured settings. You can find these settings under the Realm Settings menu item, displayed in the left-hand navigation pane. On clicking Realm Settings, various tabs are displayed in the right-hand pane.
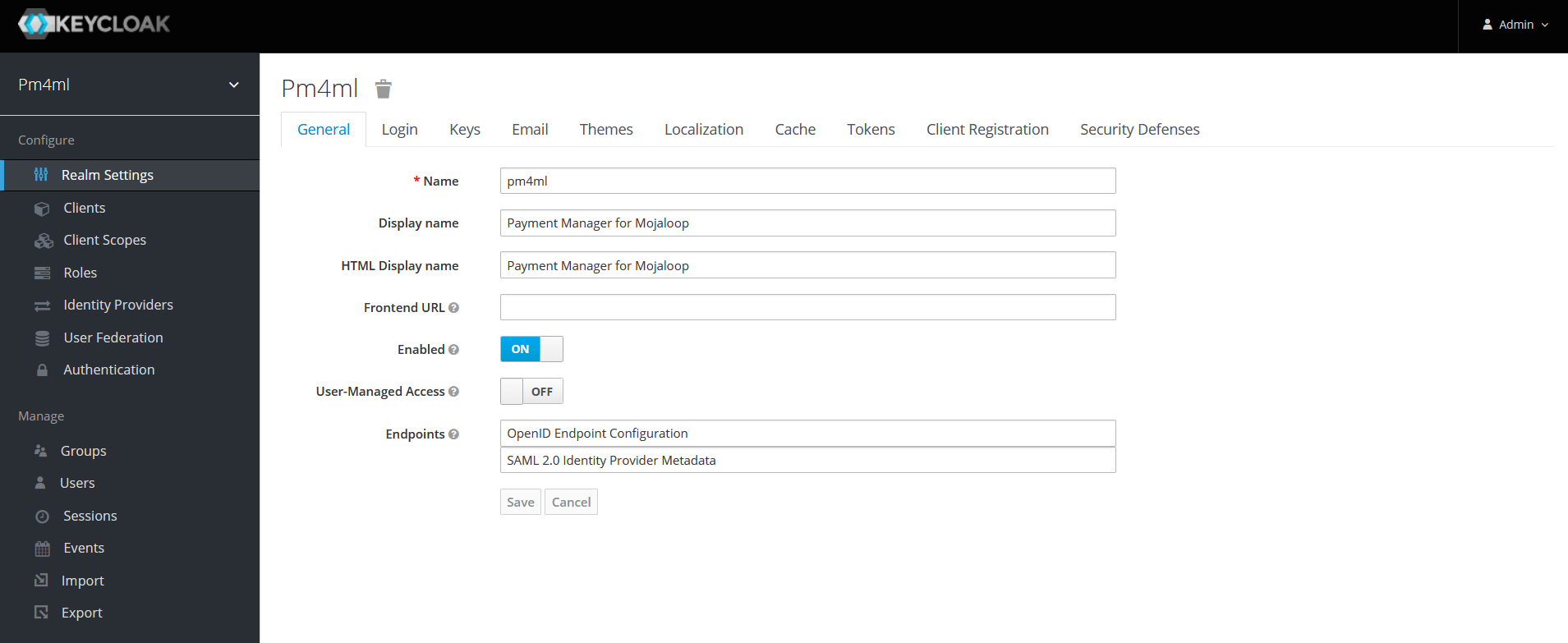
Some of the key settings on the General and Login tabs are highlighted in the table below.
| Click the links in the table to find out further details about the individual settings. |
| Tab | Setting |
|---|---|
General |
Name: This is the name of the Pm4ml realm. |
Enabled: ON |
|
Display name: Payment Manager for Mojaloop |
|
User-Managed Access: OFF |
|
Endpoints: OpenID Endpoint Configuration and SAML 2.0 Identity Provider Metadata |
|
Login |
User registration: OFF |
Edit username: OFF |
|
Forgot password: ON |
|
Remember Me: OFF |
|
Verify email: OFF |
|
Login with email: ON |
|
Require SSL: external requests |
|
Token |
The settings on this tab enable you to configure how you want the refresh of access tokens to happen, how long a session can be live or idle, and so on. |
For further information on realm settings, see Keycloak documentation.
Clients
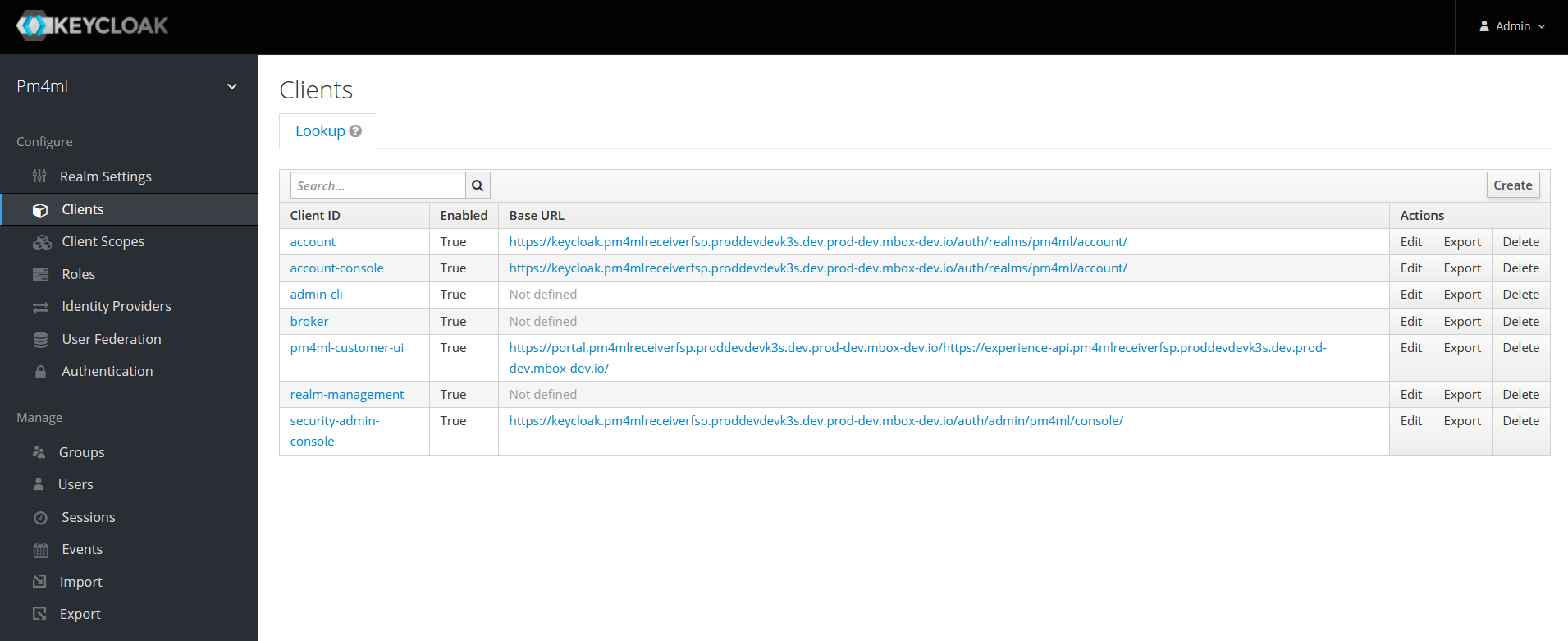
Clients in Keycloak are entities that can request the authentication of a user. The Payment Manager application is one such entity, which has to be registered to the Payment Manager realm.
The Payment Manager user interface (pm4ml-customer-ui) is registered as a client to the Payment Manager realm by default.
| Clients other than pm4ml-customer-ui are Keycloak’s own clients necessary for the correct operation of Keycloak. Do not modify client settings unless you have a particular requirement and the consequences of your actions (reduced security) are fully understood. |
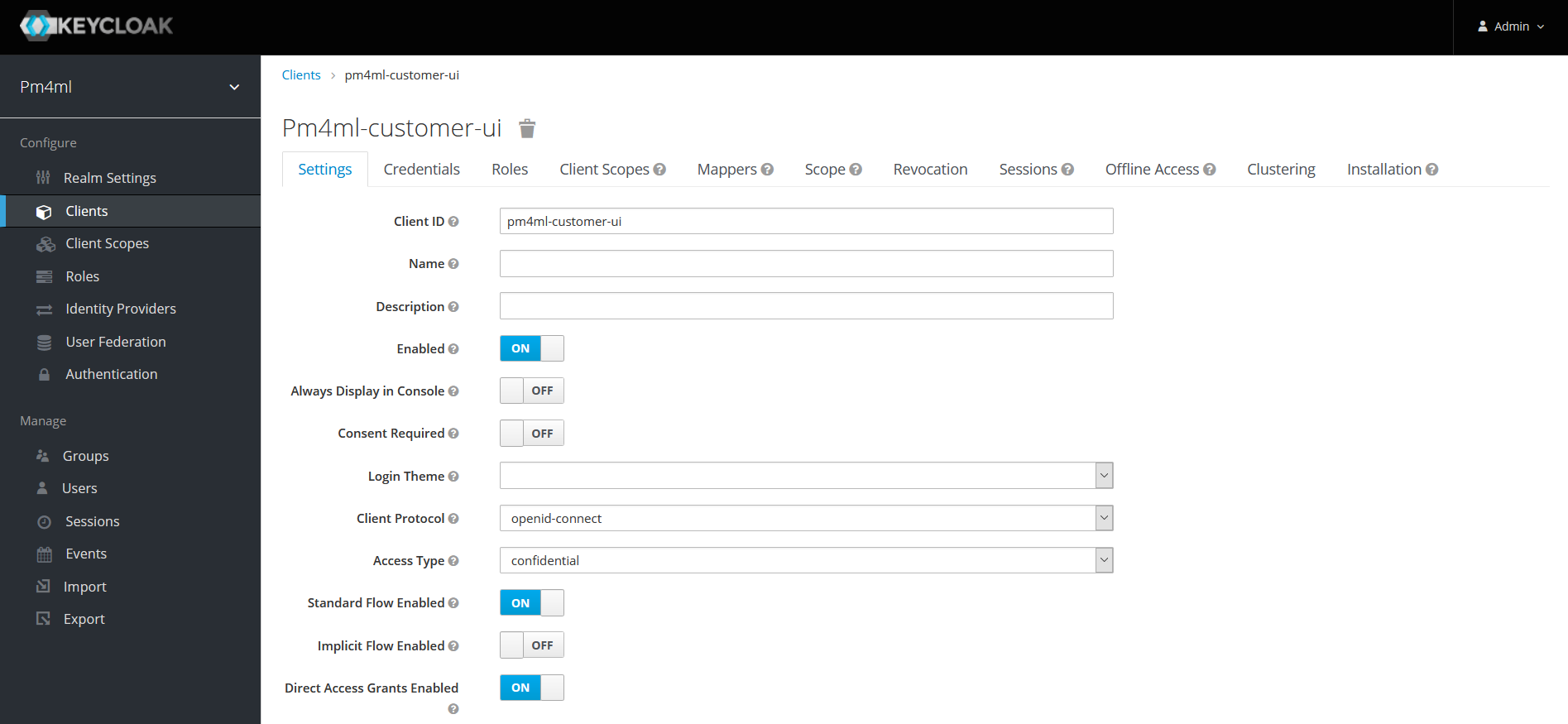
On clicking pm4ml-customer-ui, the settings associated with it are displayed. Some key settings are highlighted below.
| Tab | Setting |
|---|---|
Settings |
Root URL: Specifies the URL where the Payment Manager user interface is accessible to users of Payment Manager. |
Credentials |
Client Athenticator: Client id and Secret |
For further information on client settings, see section Clients in the Keycloak Server Administration Guide.