Managing TLS server certificates
The TLS Server Certificates page allows you to:
-
Hub Server Certificates tab: Upload the Hub’s CA-signed TLS server certificate, as well as the CA’s root and intermediate certificates.
-
DFSPs Server Certificates tab: Retrieve DFSPs' CA-signed TLS server certificates, as well as the CAs' root and intermediate certificates.
Uploading the Hub’s TLS server certificate chain
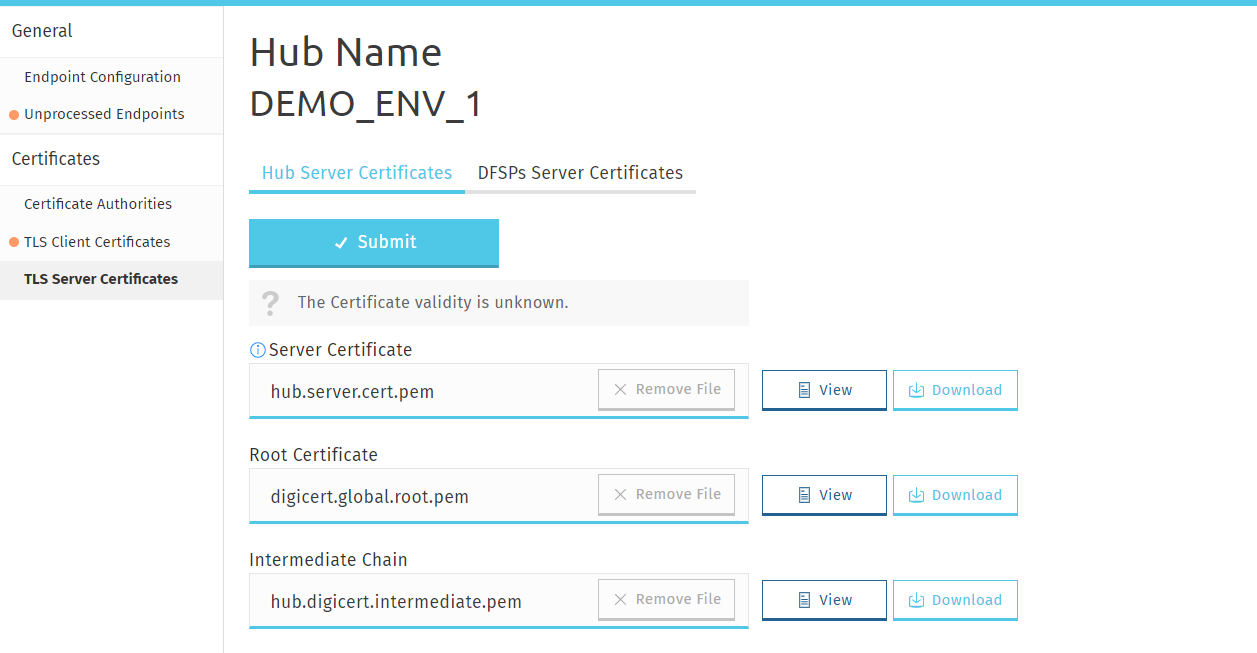
To upload the Hub’s CA-signed TLS server certificate chain:
| On uploading a certificate, MCM renames the file so that the file name includes information about: 1) the type of certificate (for example: root, intermediate, server), 2) the environment (for example: sandbox, staging, production), 3) the name of the DFSP. |
-
Go to the Hub Server Certificates tab.
-
Click Choose File in the Server Certificate field, and select your TLS server certificate signed by your CA saved on your computer.
-
To upload the root certificate of your CA, click Choose File in the Root Certificate field, and select the root certificate of your CA saved on your computer.
-
To upload the intermediate certificate of your CA, click Choose File in the Intermediate Chain field, and select the intermediate certificate of your CA saved on your computer.
NOTE: The intermediate chain must be presented as a single file. If your intermediate chain is made up of multiple files, combine them into one file in the following order: host certificate first, then the certificate that signs it, then the certificate that signs the previous certificate, and so on. Go from the most specific certificate to the least specific certificate, with each certificate verifying the previous one. -
Click Submit. On submitting the certificates, they are validated. The following details are validated:
-
The root certificate is a root certificate indeed. It can be self-signed or signed by a global root.
-
The intermediate chain is made up of valid CAs and the top of the chain is signed by the root.
-
The certificate and its chain must form a valid trust chain.
-
The certificate must have the "TLS WWW server authentication" key usage extension.
-
The certificate must be valid at the present time according to the certificate validity period.
-
The certificate key length must be 4096 bits.
-
| If you have accidentally uploaded the wrong certificate, you can re-upload a new certificate and that will replace the old one. |
Retrieving a DFSP’s TLS server certificate chain
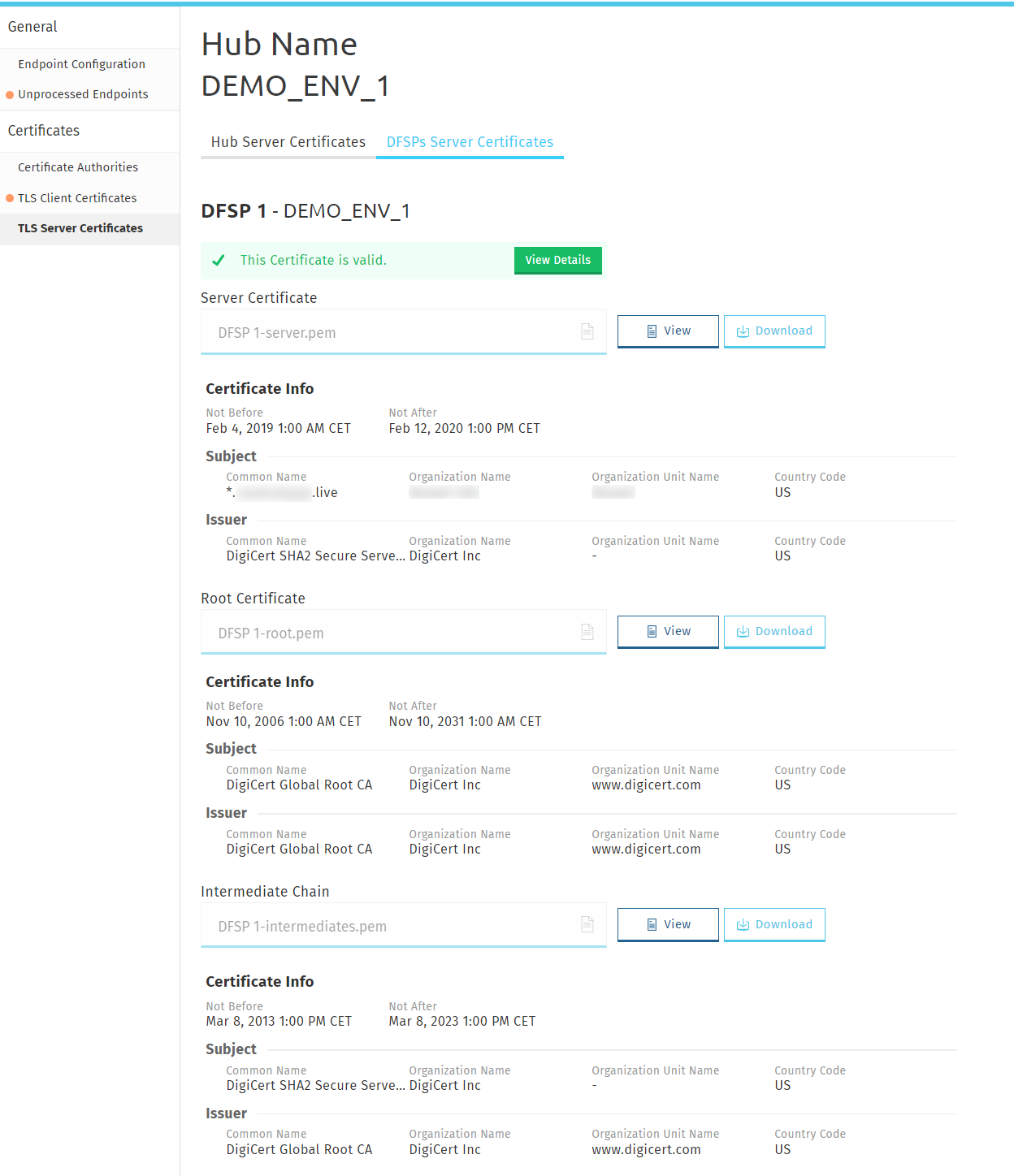
The Hub must obtain the root and intermediate certificates of the DFSP’s CA that signed the DFSP TLS server certificate. These need to be installed in the outbound API gateway.
To retrieve a DFSP’s TLS server certificate chain after they have uploaded it:
-
Go to the DFSPs Server Certificates tab.
Information about the validity of the server certificate is also displayed. Click View Details for details on validation. The following details are validated:-
The root certificate is a root certificate indeed. It can be self-signed or signed by a global root.
-
The intermediate chain is made up of valid CAs and the top of the chain is signed by the root.
-
The certificate and its chain must form a valid trust chain.
-
The certificate must have the "TLS WWW server authentication" key usage extension.
-
The certificate must be valid at the present time according to the certificate validity period.
-
The certificate key length must be 4096 bits.
-
-
Click Download for each certificate that you want to download.